Click on the minor arrow button (one) on the appropriate facet of the column titles or right mouse click on the route list.
When it comes to basic safety, the internet site’s bought a prime-notch firewall and an SSL certificate, and Epoch and Segway are there to guarantee your payment facts is safe.
For those who have set up demanding firewall policies then RDP protocol should be authorized while in the firewall filter forward chain.
Ideally with this particular data as well as web-sites offered in the following paragraphs, you'll be able to keep on with only Safe and sound porn web-sites!
The technological storage or entry which is utilized completely for statistical functions. The complex storage or access that is definitely applied exclusively for nameless statistical purposes.
If you favor your porn being more real looking and fewer fantasy-primarily based, you’re gonna adore Truth Kings. As they are saying, art imitates everyday living, and as this porn Web page’s title indicates, its porn videos resemble sex in real life.
Occasionally you may want to block certain Web sites, by way of example, deny use of enjoyment web sites for employees, deny access to porn, and the like. This may be reached by redirecting HTTP traffic to a proxy server and use an access-list to allow or deny sure Web sites.
Improvements produced to Read more window structure are saved and following time when WinBox is opened the identical column get and dimension are used.
The technical storage or obtain is necessary for the authentic objective of storing Choices that are not asked for with the subscriber or person. Statistics Figures
Port number is https://winboxplay.my/ set after the sq. brace when it's important to attach WinBox to other port than the default:
Yet another good thing about this kind of Winbox Malaysia setup is the fact that NATed purchasers powering the router are not directly connected to Click here the world wide web, that way extra defense towards attacks from outside the house mostly https://winboxplay.my/ is not really needed.
A ruleset is analogous to input chain policies (acknowledge proven/connected and drop invalid), besides the first rule with action=fasttrack-relationship. This rule enables proven and relevant connections to bypass the firewall and noticeably reduce CPU utilization.
It’s the quality of porn that bought a web-site increased to the checklist, as well, if, say, the security steps of two distinct web sites were on par.
Some of these women are products – Other people are the women you'll find on several of the most effective hookup web sites or Instagram famous people.
 Emilio Estevez Then & Now!
Emilio Estevez Then & Now! Val Kilmer Then & Now!
Val Kilmer Then & Now!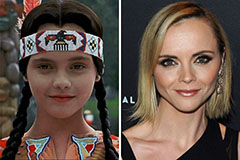 Christina Ricci Then & Now!
Christina Ricci Then & Now! Jane Carrey Then & Now!
Jane Carrey Then & Now! Richard Dean Anderson Then & Now!
Richard Dean Anderson Then & Now!